In our increasingly digital world, ensuring the security of our online accounts and data is paramount. From financial transactions to personal communications, we rely on digital platforms to manage various aspects of our lives. With the rise of sophisticated hacking tools and techniques, it’s more crucial than ever to be proactive about our digital safety. This article aims to provide insights into some essential security measures, with a spotlight on safeguarding your FYBIT account.
Complexity of Passwords: Why It Matters
One might think that a password is just a string of characters, but in the realm of cybersecurity, it’s the first line of defense. The complexity and length of your password can be the difference between keeping your account secure and falling victim to a cyber-attack.
A recent study by Home Security Heroes showcased the prowess of an AI tool called PassGAN. This tool was able to crack a staggering 51% of common passwords in under a minute. Within a day, it deciphered 71%, and within a month, an alarming 81%. The study further demonstrated that a 12-character password, composed of both uppercase and lowercase letters, would take the AI 289 years to crack. Adding numbers to the mix? 2,000 years. Throw in symbols, and you’re looking at 30,000 years.
The lesson here is clear: longer, more complex passwords are exponentially more challenging to crack. Home Security Heroes recommends using passwords of at least 12 characters, incorporating not just letters but also numbers and symbols. They’ve even developed a tool that estimates the time required to crack a given password, serving as a sobering reminder of the importance of password strength.
Visit the Home Security Heroes website and see how long it would take to hack a password similar to yours. Even though they claim, “Entries are completely private and are never saved or shared in any way,” I wouldn’t advise entering your actual password there 😉
The Risks of Public Wi-Fi
While the convenience of public Wi-Fi networks in cafes, airports, and other locations is undeniable, they present a significant security risk. Public networks are often less secure, making it easier for hackers to intercept data. When using public Wi-Fi, avoid accessing sensitive accounts or conducting important transactions. If necessary, consider using a virtual private network (VPN) to encrypt your online activities.
Two-Factor Authentication (2FA): A Second Line of Defense
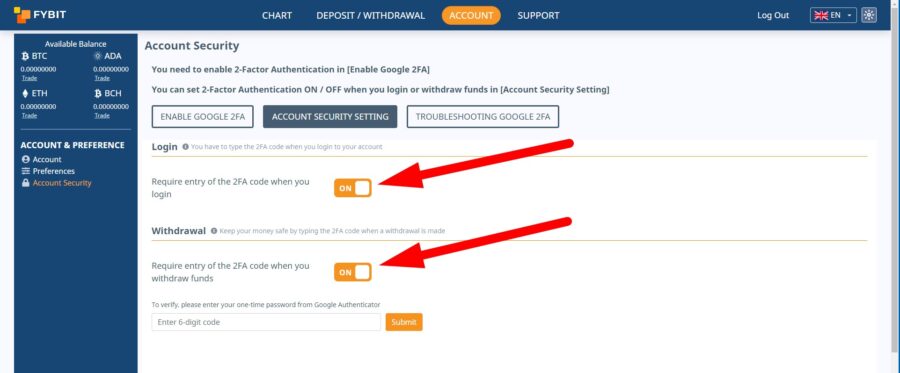
Two-factor authentication (2FA) adds an additional layer of security to your accounts. Even if a hacker manages to guess or crack your password, 2FA requires another form of verification – often a code sent to your mobile device. This dual-layered approach ensures that even if one security measure is compromised, there’s another barrier keeping intruders out.
Enable 2FA on FYBIT if you haven’t done so already.
 Phishing: Don’t Get Hooked
Phishing: Don’t Get Hooked
Phishing attacks involve tricking individuals into giving away sensitive information, often by impersonating trusted entities. These attacks can come in the form of emails, messages, or even phone calls. To combat this, be skeptical of unsolicited communications, especially those that ask for personal or financial details. Always double-check URLs (https://fybit.com) to ensure you’re on the official website and not a malicious imitation.
Safeguarding Your FYBIT Account
Fybit, as a leading crypto trading platform, understands the importance of security. Beyond the general security measures discussed, Fybit has implemented specific protocols to ensure the safety of its users:
Secure Storage: A cold wallet system guarantees the safety of your funds.
Protection against Market Manipulation: FYBIT’s index is formed from five price sources, leveraging an average price system to prevent manipulation.
High Liquidity: Ensuring immediate and complete execution of orders at the desired price.
Protection of User Information: Your personal details are guarded with the utmost care.
Furthermore, always be wary of emails or messages claiming to be FYBIT’s support, especially if they initiate contact. Official communications from FYBIT will never ask for sensitive information unsolicited.
Conclusion
In the digital age, staying one step ahead in terms of security is imperative. By understanding the risks and implementing the recommended measures, you can ensure that your online presence, especially on platforms like Fybit, remains uncompromised. Remember, the key is a combination of awareness, vigilance, and proactive defense.